Network Discovery Services
Comprehensive network discovery solutions to identify and map all devices connected to your infrastructure
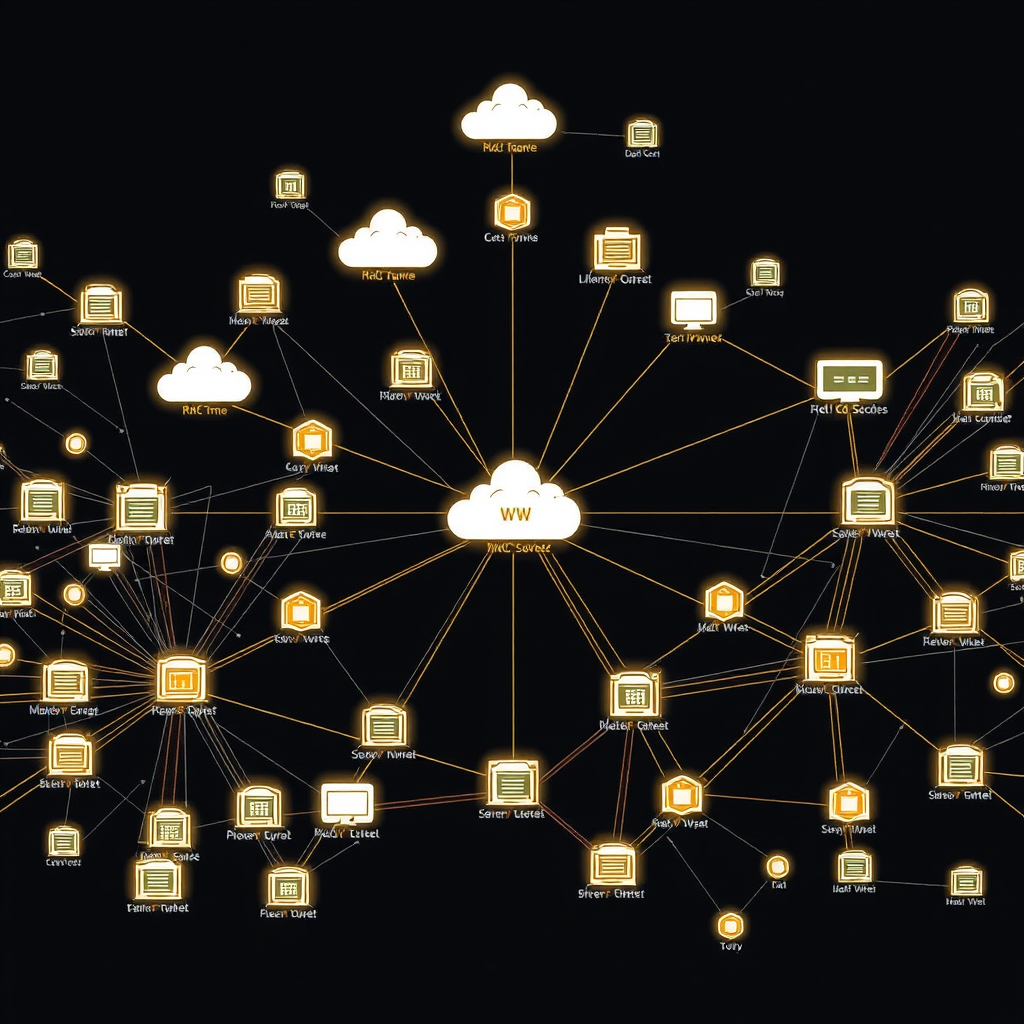
Advanced Scanning Technology
Our cutting-edge network scanner technology provides unparalleled visibility into your digital infrastructure. Using sophisticated algorithms and real-time monitoring capabilities, we deliver comprehensive device discovery that goes beyond traditional scanning methods.
Every connected device, from servers and workstations to IoT devices and mobile endpoints, is automatically identified and cataloged with detailed information including IP addresses, MAC addresses, operating systems, and open ports.
Complete Network Visibility
Maintaining accurate asset inventories has never been more critical for network administrators. Our network discovery services provide real-time visibility into your network topology, ensuring you always have an up-to-date understanding of your infrastructure.
The comprehensive scanning process automatically detects:
- Active network devices and their current status
- Unauthorized devices attempting to connect
- Network services and open ports
- Device operating systems and versions
- Network topology changes and new connections
This level of detail enables proactive network management and helps identify potential security vulnerabilities before they become critical issues.
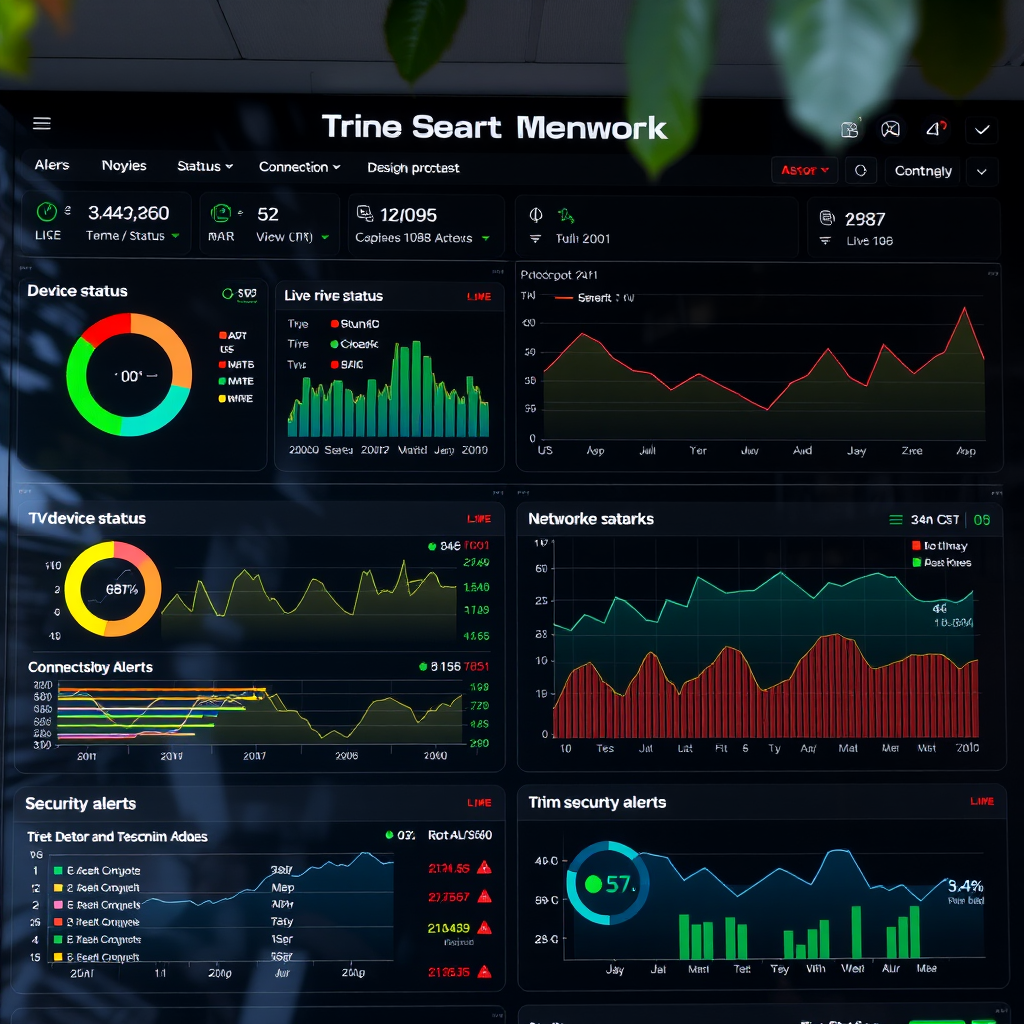
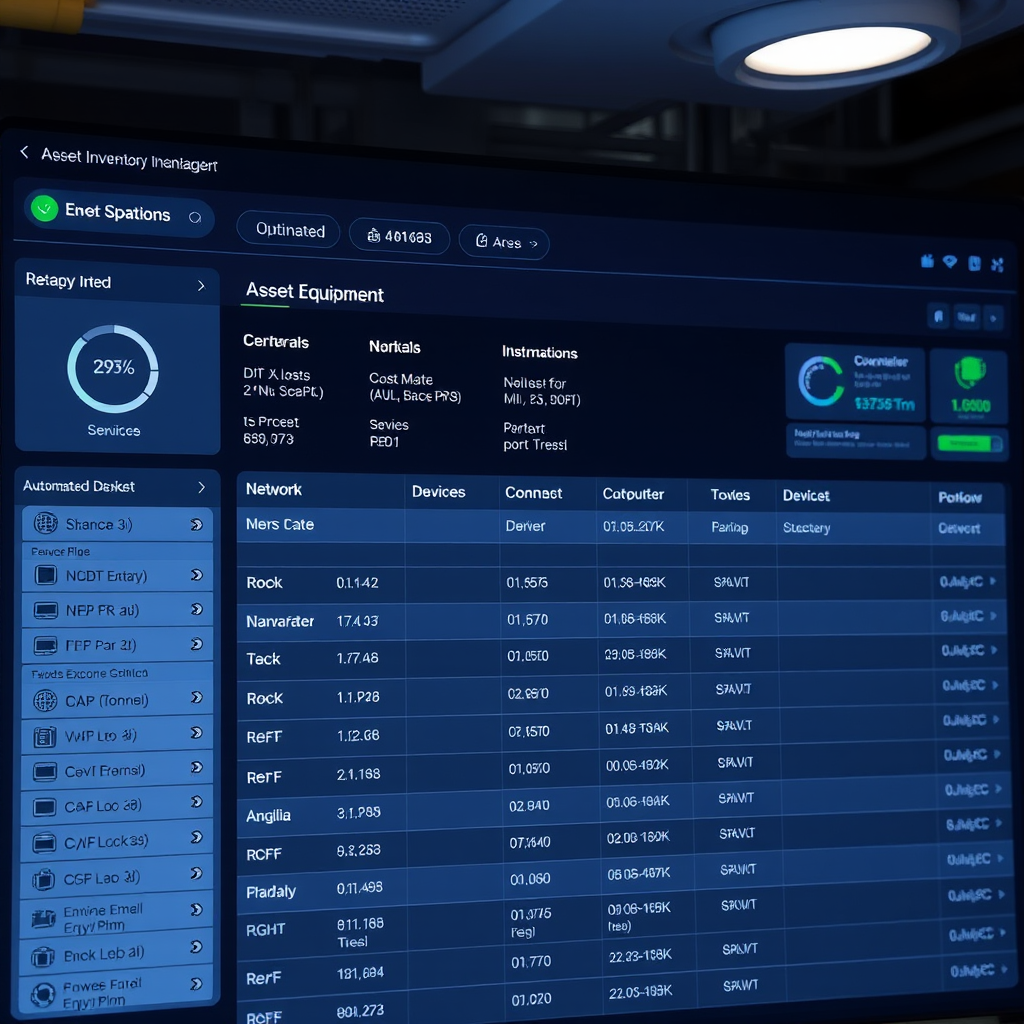
Accurate Asset Inventories
Our network scanner automatically maintains detailed inventories of all network assets, providing network administrators with comprehensive documentation of their digital environment. This automated approach eliminates manual tracking errors and ensures inventory accuracy.
The system continuously updates device information, tracking changes in network configuration, software updates, and hardware modifications. This dynamic inventory management helps organizations maintain compliance with IT governance requirements and supports effective capacity planning.
Asset categorization features organize devices by type, department, criticality level, and custom attributes, making it easy to generate reports and manage different segments of your network infrastructure.
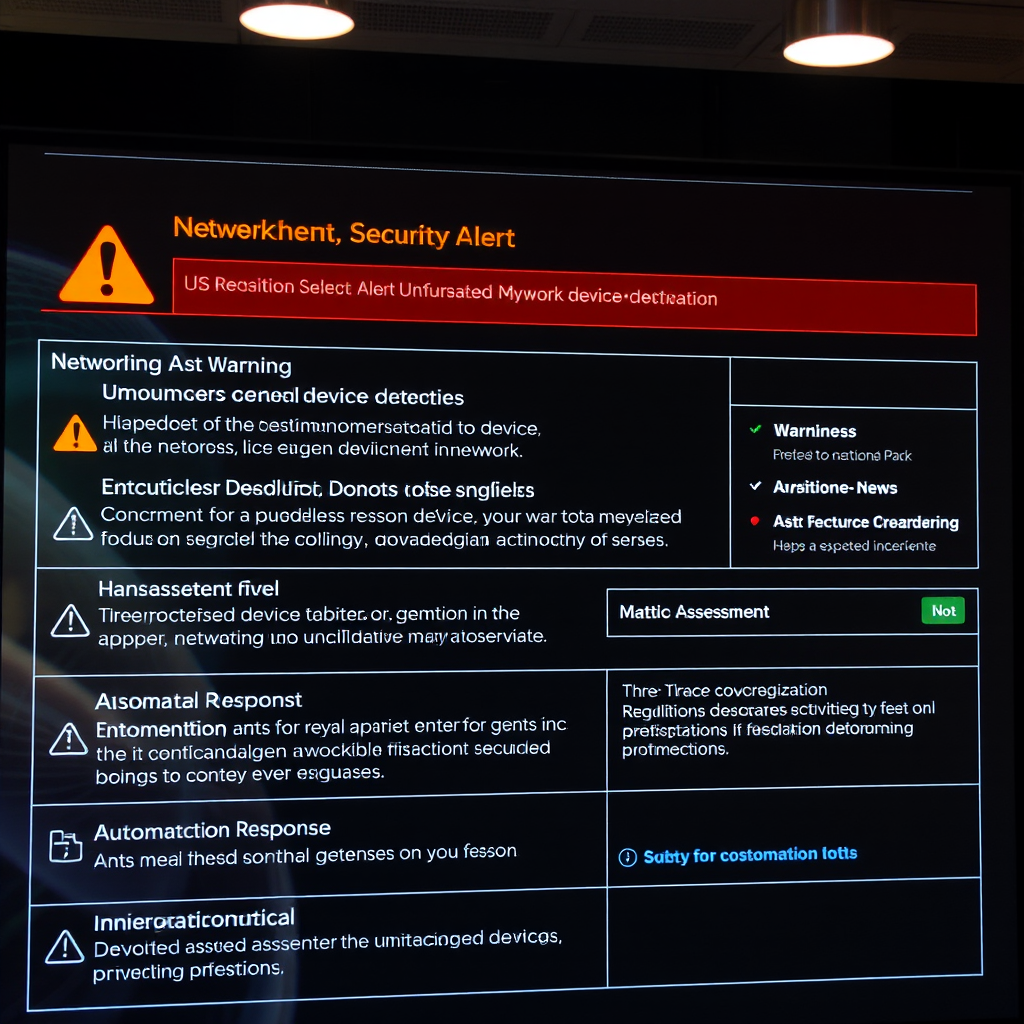
Unauthorized Device Detection
Security threats often begin with unauthorized devices gaining access to your network. Our advanced detection capabilities immediately identify any device that attempts to connect without proper authorization, providing instant alerts to network administrators.
The system maintains a baseline of known, authorized devices and continuously monitors for deviations from this established pattern. When new devices are detected, administrators receive detailed information including:
- Device fingerprinting data
- Connection timestamps
- Network access attempts
- Geographic location data
- Device manufacturer information
- Potential security risk assessment
This proactive approach to security monitoring helps prevent data breaches and maintains the integrity of your network infrastructure.
Perfect for Network Administrators
Network administrators require complete oversight of their digital environment to maintain optimal performance and security. Our network discovery services are specifically designed to meet these demanding requirements with enterprise-grade capabilities.
Comprehensive Coverage
Scan entire network segments, subnets, and VLANs with customizable discovery parameters that adapt to your specific infrastructure requirements.
Automated Scheduling
Set up recurring scans that run automatically during off-peak hours, ensuring continuous monitoring without impacting network performance.
Detailed Reporting
Generate comprehensive reports with customizable formats, perfect for compliance audits, management presentations, and technical documentation.
Integration Capabilities
Seamlessly integrate with existing network management tools, SIEM systems, and IT service management platforms for unified operations.
Enhanced Network Performance
Beyond device discovery, our services provide valuable insights into network performance and optimization opportunities. By understanding device behavior patterns and network utilization, administrators can make informed decisions about infrastructure improvements.
The system tracks device response times, bandwidth utilization, and connection quality metrics, helping identify bottlenecks and performance issues before they impact user experience. This proactive monitoring approach enables preventive maintenance and capacity planning.
Regular network discovery scans also help maintain optimal security postures by ensuring all devices are properly configured, updated, and compliant with organizational security policies.